bomonike
 This robot butler is simple, but not stupid
This robot butler is simple, but not stupid
The object of this tutorial is provide deep but succinct commentary (without marketing generalizations) as we take a carefully crafted step-by-step hands-on tour. All on a single searcheable page. NOTE: Content here are my personal opinions, and not intended to represent any employer (past or present). “PROTIP:” here highlight information I haven’t seen elsewhere on the internet because it is hard-won, little-know but significant facts based on my personal research and experience.
Overview
- Why Ansible?
- SSH
- Owned by Red Hat
- Ansible Tower
- install postgresql-server & run postgresql-setup command
- Alternatives to Ansible
- Ansible functionality
- Exam prep
- Install Ansible
- Configure Ansible Server
- Configure host nodes
- Ansible-Galaxy Roles
- Modules
- Steps Modules do
- Templates
- Role files
- Tasks
- Windows support
- SSH into Hosts
- Python Ansible Control Server on Linux, not Windows
- Playbooks
- Config. settings
- Include files
- Roles
- Daemon Sets
- Rolling updates
- Social Community
- Tutorials
- Certifications
- Videos
- Misc
- Resources
- More on DevOps
Why Ansible?
Ansible is not a configuration management system like Jenkins.
Ansible is an infrastructure management system like Terraform, Puppet, Chef, Salt.
The Ansible Project (https://docs.ansible.com/) (Ansible Core) was identified as, among the hundreds of thousands of repositories in GitHub, #7 most contributors and most discussed projects (in front of even Kubernetes, npm).
-
Mentions in Reddit Hacker News (HN) forum show higher uptake in Ansible vs. other configuration management solutions:

BTW The name “ansible” is popularized by the science-fiction book and movie “Ender’s Game” which uses what it calls an “ansible” to communicate, in real-time, with many ships at once, to many galaxies far away.
The objective of building an Ansible Managed Environment is to configure software of many host nodes using “declarative” YAML code within “playbooks” instead of manual configuration on individual nodes.
When the ansible program is invoked, it delegates work to various Modules. Additional custom modules can be defined, such as for building assets within AWS using CloudFormation as well as other clouds (Digital Ocean, Linode, Rackspace, etc.).
ansible is one of the command-line executables installed by Python when the Ansible (Core) Control Server is installed.
“Ansible Core” since version 2.13 only contains core (essential) modules. It’s legacy “Ansible Engine” in RHEL 8.5 and earlier includes 3367 modules by default.
“Core” in RHEL 8.6 and later installs additional modules through collections from the ansible-galaxay at https://galaxy.ansible.com website, which is a community-submitted repository of Roles that define the installation of many categories of software (database, etc).
The website shows a “quality rating” based on runs of the ansible-lint program which validate changes. The program used on by the website can be run on your server after being installed by pip to validate changes after downloading and editing.
Files in the Galaxy are versioned in a GitHub repository files can also be pulled by the ansible-pull program which (like Git) can pull other files such as the inventory of host nodes to be populated. Inventory files are managed by the ansible-inventory executable. Among downloads can be (dyn) programs that act like a static inventory file, but dynamically retrieve inventory data.
is a dependency of the Ansible Tower which provides an API and GUI front-end to the open-source Control Server. It has a command line interface and web-based interface for managing Ansible projects using role-based access control, job scheduling, and real-time job status updates. For small to medium-sized environments.
SSH
The use of SSH (Secure Shell) is Ansible’s differentiatior. This is the approach that makes Ansible easy and secure because the SSH utility comes standard in all Linux distributions for users to communicate with servers. SSH uses a commonly open port 22, one does not need to beg for special ports to be opened through the enterprise firewall (which one needs to do with custom agent programs used by Chef, Puppet, and others.
Use of SSH does require the Linux ssh-keygen program to create pairs of “cryptographic” key files. The public key is copied to each host node created. This does not compromise secrets because the private key stays on the machine where the pair is created. The SSH program encrypts communications with its private key for the receiver to decrypt using the public part of the key pair.
By default, JSON messages are communicated back to the Control Server’s API listening on standard port 80. Internally, Ansible uses the Django-REST framework, PyYAML.
Various modules run on remote hosts provide the plumbing for other networking protocols, such as HTTP, runing on remote machines.
Ansible plug-ins can also be downloaded and installed so Ansible can communicate via ZeroMQ “fireball mode” or other means.
WinRM
To connect with Windows machines, Windows Remote Management (WinRM) is used (from Vista SP1 or Windows 2008 R1 and up).
Other
Windows modules include win_feature (to install and uninstall Windows Features) and
win_regedit (Add, Edit, or Remove Registry Keys and Values). WinRM python module
Tasks, Plays, Playbook
Modules are invoked by a series of Tasks defined as plays in playbooks.yml files.
Instead of using a database server, Ansible stores declarations in text files of yml format (pronounced as “yamil”) that are both human and machine readable. So Playbooks can be edited by any text editor.
A task can trigger handlers (shell scripts) which run on some condition, usually once at the end of plays.
Plays map a group of hosts to roles. Each role is like a (subroutines) which make code in playbooks reusable by putting the functionality into generalized “libraries” that can be then used in any playbook as needed.
The ansible-playbook program manages playbooks.
ansible-vault encrypts and derypts entire playbooks.
ansible-console can execute individual tasks (during debugging).
Within each host node, a facts.d in created within the /etc/ansible folder.
Finally, the ansible-doc executable presents additional information.
Recap:
Owned by Red Hat
The @ansible Twitter account is titled “Red Hat Ansible” because it’s initiating author, Michael DeHaan from North Carolina (@laserllama), began writing Ansible in his spare time in 2006 while working at RedHat (after a stint at Puppet). His AnsibleWorks got acquired by RedHat in 2015. See the slides to his video Python-Powered Radically Simple IT Automation” at PyCon 2014.
His advice at All Things Open lightning talk Dec 3, 2014:
- “Your IT infrastructure should be boring”
- “How do we get sysadmins and developers together to cheat off each other, even at competing companies”
- “Automation should not be your day job”
- “Build early and often. Build a culture of testing.”
- “Have Dev/QA/Stage environments that mirror production to see what can go wrong early.”
docs.ansible.com lists the major aspects of Ansible:
-
Ansible Network (ecosystem) lists overview books and videos.
-
Ansible Tower builds on top of Ansible Core provides user provisioning and audit trails running playbooks, all done within a web UI. It is licensed (beyond 10 hosts).
-
Ansible Galaxy is a website, like GitHub, an API-powered community-submitted repository of Roles (subroutines) which make code in playbooks reusable by putting the functionality into generalized “libraries” that can be then used in any playbook as needed.
-
Ansible Lint validates playbook contents.
Ansible Tower
VIDEO: Red Hat (IBM) Ansible Tower adds a web server UI for “push button deployment” to manage projects (set of playbooks).

For example, checking “ENABLE PRIVILEGE ESCALATION” is the same as adding -b in ansible ad-hoc commands.
Tower installs within Linux base configurations at /etc/tower/settings.py.
Look at this after install.
PROJECTS_ROOT
Ansible Tower makes use of a PostgreSQL database, either locally, remotely, or in a HA inventory group cluster. Tower provides Role Based Access Control (RBAC) to acccess its database via REST API.
Ansible Automation Platform
Red Hat’s Ansible Automation Platform includes Ansible Tower as one of its components to provide a comprehensive suite for enterprise-level automation of large-scale operations and complex environments (thousands of nodes). It provides an Automation mesh for distributed deployments with high availability through clustering and performance monitoring across clusters.
Ansible Lightspeed
Ansible Lightspeed can do:
- Single and multitask generation
- Generate Playbooks
- Explain Playbooks
- Content source matching
- Content maintenance and modernization
- Monitoring through Red Hat Hybrid Cloud Console Admin Dashboard
To use GenAI services to make it easier to create and manage Ansible playbooks, add to Ansible Lightspeed IBM Watsonx Code Assistant’s training models to generate code. Ansible is one of 100 languages supported by WatsonX Code Assistant. Lightspeed can use Ansible-specific custom IBM Watsonx Granite LLM models. Assistant tools to make it easier to create and manage Ansible playbooks.
Ansible Lightspeed is a paid VS Code extension add-on for Ansible Automation Platform. A separate license of Ansible Lightspeed and Ansible Automation Platform (AAP). A free 90-days license of Lightspeed “Cloud Pak for Data” is available. After that, it’s a minimum of $ 1,500. A developer license option to use AAP doesn’t count as a valid license for AAP + Lightspeed.
Ansible Lightspeed is offered on both on-premises and in a cloud hosted by IBM.
- Request a trial for Ansible Automation Platform (not through developers.redhat.com)
https://cloud.ibm.com/catalog/services/ibm-watsonx-code-assistant - install:
sudo dnf install python3-pip ansible-corehttps://github.com/monfresh/laptop my personal playbooks and scripts to install a laptop from scratch including some dotfiles. Based on Fedora 27. Not idempotent.
https://github.com/vaskas/laptop-ansible for Fedora 26
- install the Ansible development package:
python3 -m pip install ansible-dev-tools --no-input - Download VS Code from visualstudio.com
- Run the RPM installer and start VS Code
- From the left side, open the Extension option
- Search for the Ansible extension and click Install
- This adds an Ansible icon in the left toolbar. Click it
-
Click the Link “Create Ansible environment” in the upper left corner
From a terminal, create a directory: mkdir ansible
- In VS Code, select File > Open Folder and open the ansible directory you just created
- Open a new file in this directory and start typing YAML code
-
In Ansible Development Tools, select Settings and have a look at the settings that are available
- In the VS Code plugin, select Settings > Ansible Lightspeed
- Ensure that all options are selected
- In the Ansible Lightspeed settings, click Connect. VS Code shows a pop-up where you need to allow the extension to sign in.
- Check your browser if no pop-up shows!
-
You’ll be connected, once you use it for the first time, you’ll be prompted to request a 90 days trial license
- Create a yml file, and use name: for the task that you want to create
- The argument to name: should be a complete description of what you want the task to do
- name: install postgresql-server
- Press Enter to generate the task, which by default will be all grayed-out
- Press Tab to convert the commented-out task to real code
- Press Escape to ignore the code suggestion
- To create a multitask request, start the request with a #, separate the requests with an &, and do NOT include - name:
-
install postgresql-server & run postgresql-setup command
-
See the Lightspeed plugin working for about 5 seconds each task. Once done, code will be generated
View Lightspeed Sources:
- Select View > Open View
- Scroll down to see Lightspeed training matchs
- A new pane opens, where sources can be clicked open to get more details
Alternatives to Ansible
-
“Comparison of open source configuration management software” on Wikipedia
-
This mentions the free Remote Execution Enabler for PowerShell tool from Solarwinds.
-
Ansible & Docker Make Chef & Puppet Unnecessary by John Minnihan (@jbminn, jbminn@modernrepo.com) Slidedeck
-
Chef vs. Puppet vs. Ansible vs. Salt - What’s Best for Deploying and Managing OpenStack?
Ansible functionality
- Provisioning - install software, patch security, copy files in, customize configurations, start web service.
- Change management of configurations with configuration remediation. Ansible evaluates to mark changed states.
- Automation - make decisions. A single change can impact several machines.
- Complex Orchestration of dependencies.
Exam prep
Linux Academy has the most complete set of video classes on Ansible:
Stosh Oldham’s video prep class [21:24:31] with diagrams and sample practical exams for the 4-hour $400 Red Hat Certified Specialist in Ansible Automation (EX407) tasks based on Red Hat® Enterprise Linux® 7.5 and Ansible 2.7:
- Create Ansible inventory filies to define groups of hosts
- Create Ansible playbooks to configure systems (hosts) to a specified state
- Create and use Ansible (Jinga2) templates to create customized configuration files for hosts
- Create Ansible roles stored in Ansible Galaxy
- Use Ansible Vault in playbooks to encrypt and decrypt sensitive data
Mercifully, Tower is not a significant requirement in the exam.
Install Ansible
Due to the transition from Ansible to Ansible Core:
- RHEL 8:
sudo subscription-manager repos --enable=ansible-2-for-rhel-8-x86_64-rpms sudo yum install ansible - RHEL 9:
sudo subscription-manager repos --enable=rhel-9-for-x86_64- appstream-rpms sudo dnf install ansible-core - CentOS Stream / Fedora:
sudo dnf install ansible-core - Ubuntu:
sudo apt install ansible-core
-
Know what version may be installed already:
ansible --version
The response for the version at time of writing (substitute “$USER” with your own account name):
config file = None configured module search path = ['/Users/$USER/.ansible/plugins/modules', '/usr/share/ansible/plugins/modules'] ansible python module location = /usr/local/Cellar/ansible/2.8.0/libexec/lib/python3.7/site-packages/ansible executable location = /usr/local/bin/ansible python version = 3.7.3 (default, Mar 27 2019, 09:23:15) [Clang 10.0.1 (clang-1001.0.46.3)]
NOTE: Ansible makes use of Python, so install that.
If you don’t see the above and instead see “command not found”, continue:
-
If you’re on a Mac, install XCode.
-
On MacOS, on any folder location, after Homebrew installed:
brew install ansible
To update Ansible:
sudo pip install ansible --upgrade
-
On Red Hat operating systems:
sudo yum -y install ansible
-
On Ubuntu, see https://crunchify.com/systemd-upstart-respawn-process-linux-os/ about using
systemd, the service management utility in all latest version of Linux distribution such as Ubuntu OS, Redhat OS, CentOS.VIDEO: Installing Ansible on Ubuntu from GitHub:
sudo apt-add-repository -y ppa:ansible/ansible sudo apt-get update sudo apt-get install -y ansible
- Skip to Configuration instructions.
Setup Vagrant and Virtualbox
-
Download and install:
- A virtual image manager from VagrantUp.com (87.9 MB for vagrant_1.8.1.dmg).
- A vm provider (hypervisor) to run virtual machines from Oracle’s VirtualBox
-
Verify availability from a command-line Terminal:
vagrant
vboxmanager -
Create a folder (of any name) for Ansible configuration files. This is typically for a project. This can be in a git folder if you’d like version management.
cd ~
mkdir ansible
cd ansibleThe ~ (tilde character above) refers to your home folder.
-
Switch to an internet browser to open a repository of Vagrant server base images:
http://vagrantcloud.com (which redirects to a site owned by hashicorp, who owns Vagrant, thus the advert for the Atlas licensed product)
NOTE: Many enterprises instead use an internal repository.
-
In the box under “Discover Vagrant Boxes”, search for ubuntu or CentOS, etc.
-
Choose one and copy its text in blue, such as “nrel/CentOS-6.5-x86_64” from contributor nrel or “ubuntu/trusty64”.
-
Close down any process making use of port 8080, as that’s Vagrant’s default port. (Jenkins also uses port 8080 by default)
-
Initialize a Vagrantfile for use by Vagrant:
vagrant init
Sample response:
A `Vagrantfile` has been placed in this directory. You are now ready to `vagrant up` your first virtual environment! Please read the comments in the Vagrantfile as well as documentation on `vagrantup.com` for more information on using Vagrant.
-
If you have a file named Vagrantfile from another source, copy it into the folder to replace the file generated.
Alternately, open a text editor to create a file name Vagrantfile in end up with this sample content to specific the acs (Ansible Control Server), web, and db servers:
Vagrant.configure(2) do |config|
config.vm.define "acs" do |acs|
acs.vm.box = "nrel/CentOS-6.5-x86_64"
acs.vm.hostname = "acs"
acs.vm.network "private_network", ip: "192.168.33.10"
end
config.vm.define "web" do |web|
web.vm.box="nrel/CentOS-6.5-x86_64"
web.vm.hostname = "web"
web.vm.network "private_network", ip: "192.168.33.20"
web.vm.network "forwarded_port", guest: 80, host: 8080
end
config.vm.define "db" do |db|
db.vm.box = "nrel/CentOS-6.5-x86_64"
db.vm.hostname = "db"
db.vm.network "private_network", ip: "192.168.33.30"
end
end
The (2) in Vagrant.configure(2) configures the configuration version.
Names between | (pipe) characters provide handles to identify each server.
Two spaces are used to indent.
Internal IP addresses (192.168.33.xxx) are used in this example.
Change 8080 to another port if it is already used by another process on your computer.
Vagrant up
- Navigate to a folder containing a Vagrantfile specification file.
-
Bring up a machine based on the Vagrantfile in the folder:
vagrant up
This can take several minutes if this is the first time, since images for servers specified need to be downloaded.
-
Switch to a Finder to see that a .vagrant (hidden) folder has been added. Under the machines folder is a folder for each type specified between pipe characters (acs, web, db, etc).
-
Open another terminal shell to check what is running:
vboxmanage list runningvms
The response are hashes:
"ansible_acs_1463860205025_4852" {128ce450-8384-4adb-a4fd-7f4ac5c1f0b8}
"ansible_web_1463862332570_44406" {dd044db3-ecf1-4b9b-9c42-96952172bd4d}
"ansible_db_1463882256962_22323" {411c8704-f220-4188-8b94-d1bfb093e1b4}
Provision Ansible Control Server
-
SSH into the acs server via vagrant:
vagrant ssh acs
This takes several seconds to connect.
This adds the ey to the known_hosts file within the .ssh folder for future reference.
-
When you’re done:
exit
-
Use a package manager to download bits. On a CentOS or RHEL server:
sudo yum -y install ansible
Alternately, on a Debian Ubuntu server:
sudo apt-get -y install ansible
Notice the log says Python is installed as well.
-
Verify:
ansible --version
Provision web server
-
SSH into the web server via vagrant:
vagrant ssh web
-
Use a package manager to download bits:
sudo yum -y install epel-release
Install by Compiling Source Code
-
Install the C-language compiler used with Python:
sudo yum install gcc
sudo yum install python-setuptools
sudo easy_install pip
sudo yum install python-devel
sudo pip install ansible
Configure Ansible Server
Linux machines instead install to:
/etc/ansible
But on Macs, as with all program installed on a Mac by Homebrew:
- A link to the
ansibleprogram is installed in folder/usr/local/bin/ - Links to the latest version of Ansible is in
/usr/local/opt/ansible - Links are also in
/usr/local/var/homebrew/linked/ansible /usr/local/lib/python2.7/site-packages/ansible- Various versions of actual Ansible files are installed to
/usr/local/Cellar/ansible
Ansible executables
-
Install the tree command if you haven’t already:
brew install tree
-
Construct the command to list files down to the 2nd level of the folder tree:
tree /usr/local/Cellar/ansible/2.8.0 -sh -L 3 | less
Press Enter to display more lines, q to quit.
The programs that can be executed on the CAS CLI console are:
- ansible -
- ansible-config -
- ansible-connection -
- ansible-console -
-
ansible-doc -
- ansible-galaxy -
- ansible-inventory -
- ansible-playbook -
- ansible-pull -
- ansible-vault -
Configure host nodes
Ansible works under the concept of “idempotance”, where repeated executions of the same script results in the same state at the end of each run. If something doesn’t exist, it is created. If something does exist already, it is left alone and another isn’t created.
A function is “idempotent” if repeated applications has the same affect as a single (initial) invocation.
Ansible reads declarations of desired state (what is wanted after processing) rather than imperative programming commands (to do this and that in a specified sequence). This is like when you get in a taxi and you provide a destination address rather than providing turn-by-turn directions to that location.
This makes definitions more reusable.
Ansible-Galaxy Roles
-
Install the Ansible-Galaxy CLI Python library:
pip install ansible-tower-cli
-
To download a particular role file from https://galaxy.ansible.com in the format:
ansible-galaxy install username.role_name
Example:
ansible-galaxy install elastic.elasticsearch
CAUTION: When deleting roles, its dependencies are not deleted automatically, leaving orphans not used by roles that remain.
Modules
Core Modules listed alphabetically:
- ad-hoc - one-line commands executed by the ansible binary (instead of running a Playbook)
- archive & unarchive
- copy - copy files from src to dest. also change mode
- file - create, rename, delete files
- get_url
- git - interact with git repositories
- group
- lineinfile - changes an existing line using a back-referenced regular expression
- mount - drive (in Tower)
- ping - validate server is up and reacheable using ICMP protocol
- playbooks
- replace
- service - control daemons, provided name and state
- setup - gathers ansible facts
- shell & command
- user - manipulate system users
- apt, apt_key, apt_rpm, yum - use package manager
-
Get documentation on a specific module:
ansible-doc lineinfile
Press q to quit out of list.
VIDEO see http://docs.ansible.com/ansible/latest/modules/modules_by_category.html
ad-hoc commands
-
Run ansible without parameters to get list of options:
ansible
-
Install software on host:
ansible node1 -i ansible/inv.ini \ -b \ -m yum \ -a "name=httpd state-latest" \ -f 100
node1is the host name-bspecifies “become user” to avoid permission errors by using elevated root permissions-ispecifies the iinventory file and its path-bspecifies user-m yumspecifies the module yum command-a "name=httpd state-latest"specifies the arguments to the ansible program saying install the latest version of httpd (http daemon web server)state=absentis specified instead to remove the program, since Ansible is declarative.-fspecifies the number of forks running copies of Ansible simultaneously“SUCCESS” is the expected response.
- Check system properties (disk space, RAM)
-
Check system performance
- Check log commands
- Check daemon up/down
- Process management
Steps Modules do
- Gather facts on hosts into variables such as ansible_os_family.
- Fetch md5 checksum from remote to verify downloaded file
- Create and manage local users and groups
-
Enable and disable OS features and preferences
- Fetch files from remote sites
- Install software (web server, app server, database, virus scanner, etc.)
- Update software security patches
-
Copy app configurations
- Copy files into server
-
Call databases to retrieve data
- Enable service to start on reboot
- Start web service
- Deploy load balancer configurations (put in or take out server on rotation)
Playbooks
Let’s look at a playbook with full annotations:
Ansible with Cloud Formation
Book Ansible for AWS ($19.99+) by Yan Kurniawan provides Ansible playbook examples:
- vpc_create.yml
- sg_empty.yml to create empty security groups.
- sg_modify.yml to modify security groups for each type of server
- sg_delete.yml
- ec2_vpc_web_create.yml to launch an instance in a particular subnet
- ec2_vpc_db_create.yml without assigning a public IP address
- nat_launch.yml to launch a “staging_nat” paravirtual t1.micro instance (with AMI name that includes “amzn-ami-vpc-nat”)
- vpc_delete.yml
- vpc_create_multi_az.yml
- sg_jumpbox.yml
- ec2_vpc_jumpbox.yml to launch jump box instance in public subnet A
- ansible -i ec2.py tag_class_jumpbox -m ping
- sg_openvpn.yml still requires manual retrieval of the AMI ID on https://openvpn.net/index.php/access-server/docs.html
Tweets about the book, #ansible4aws, is inactive since 2016 when the book was done.
The book provides an Ansible module in folder: library/vpc_lookup
- an update of https://github.com/edx/configuration/blob/master/playbooks/library/vpc_lookup (from John Jarvis) to lookup a VPC or subnets ID stored in local (safe) folder based on a particular filter specified in a script.
PROTIP: Each Ansible module is associated with a command, and return JSON.
PROTIP: Disable host key checking in ssh configuration so ssh will automatically add new host keys to the user known hosts files without asking (the default is “ask”).
- Disable host key checking with StrictHostKeyChecking set to “no” in /etc/ssh/ssh_config file.
View sample configurations
-
Use an internet browser to open https://galaxy.ansible.com/search?deprecated=false&order_by=-relevance&keywords=
-
Search.
-
Open a sample playbook.
Playbooks are defined in .yml files, which begin with three dashes in the first line.
Playbooks define plays. consisting of one or a set of tasks.
tasks invoke modules.
Tasks trigger handlers which run on some condition, usually once at the end of plays.
Spaces after dashes and colons are required.
An Ansible Config define Ansible control server configuration.
Jeff Geerling
Notice the repos downloaded more than anyone is by @geerlingguy, Jeff Geerling (all around nice guy and Drupal expert jeffgeerling.com who has been contributing to Ansible community since early 2013.
In addition to series on Raspberry Pi and Drupal, he wrote ansiblefordevops.com completed 2020-05-13 on LeanPub).
Code for the book is at https://github.com/geerlingguy/ansible-for-devops, which has an issue for each of 15 episodes of his Ansible 101 series on YouTube. He has chapter markers into each video at his blog plus Q&A (written in Markdown).
-
Introduction to Ansible 2.9.6 and Python 3.7.6 on CentOS via dhcp.
“DevOps is a philosophy”. Use
pip3 install ansible -
BOOK chapter 5.
Inside the Ansible main.yml:
API_KEY: ""
To encrypt a file [15:16] replaced it with:
ansible-vault encrypt vars/api_key.yml
[17:40] Reference a password file:
ansible-playbook main.yml --vault-password-file ~/.ansible/api-key-pass.txt
[18:05] Re-Encrypt with a new key without decrypting:
ansible-vault rekey vars/api_key.yml
ansible-playbook main.yml --ask-vault-pass
Include another file with
import_tasks: tasks/apache.yml
Jeff’s https://github.com/geerlingguy/mac-dev-playbook provides tools to install executables on MacOS using Ansible.
https://github.com/geerlingguy/ansible-role-dotfiles
Ansible Vault Encryption
-
To encrypt a file so it can be stored in a repository such as GitHub:
ansible-vault file \ --ask-vault-password no_log
no_logcensors log output.Adding
rekeyresets the password.
Encrypted data within playbooks stored in GitHub can be unencrypted in memory using Ansible Vault.
Templates
In the templates folder are Ansible template files which specify values which resolve variables defined in other files, such as: ``.
---
hosts: webservers
tasks:
- name: ensure apache is at the latest version
- yum: name=httpd state=latest
- name: write the apache config file
template: src=/srv/httpd.j2 dest=/etc/httpd.conf
Template files have the .j2 file extension because they are processed by the Jinga2 templating program that comes with the Ansible installer. Written in Python, Jinga2 is also by Django, Flask, and other Python frameworks.
Role files
Role files encapsulate instructions on how Ansible performs a discrete unit of work, such as building a webserver.
A role folder contains sub-folders with these names:
acme_sample/
webserver/
README.md
defaults/ - entered vis main.yml
files/
handlers/ - tasks flagged to run using the notify keyword
meta/main.yml - role dependencies and configurations such as allow_duplicates
tasks/
templates/
tests/
vars/
The main.yml in meta defines dependencies:
---
galaxy_info:
author: John Doe
description: Quick and easy acme web installer.
company: Acme
license: MIT
min_ansible_version: 1.9
platforms:
- name: EL
versions:
- all
galaxy_tags:
- acme
- installer
- web
dependencies:
- { role: username.common, some_parameter: 3 }
- { role: username.iptables, open_port: 80 }The role_use.yml file?
Tasks
Ansible tasks are commands executed from command line terminals.
Tasks are shereable and repeatable.
Inventory file
Ansible inventory files lists hosts can be defined within:
/etc/ansible/hosts
The folder contains .ini format or yml format:
[webservers] 192.168.33.20 192.168.33.30 ansible_connection=ssh ansible_user=mpdehaan [webservers:vars] webserver_port=2222 [db] db-a.example.com [lbservers] lbserver http_port=80 maxRequestsPerChild=808 [monitoring] nagios
Group names are defined within square brackets. Groups are referenced in playbooks.
Variables applicable to all items within a group can be defined. What’s wrong with the example?
To get the status of servers under [webservers] in the inventory file above:
ansible webservers -m ping
PROTIP: Inventory files should not contain variables.
In addition to this ad-hoc run, Ansible can be run based on the contents of Playbooks with a command such as:
ansible-playbook file.yml
Add -v for more detailed response.
Such inventory files are typically kept in a Git repository.
Inventory files can be dynamic, issued by a program that returns to STDOUT. Examples is Cobbler, LDAP, cloud such as AWSEC2, retrieving from CMDB, etc.
ansible all -l dynamic.py -m ping
Notice two parameters: -l (--list) and --host.
There are two arguments a dynamic inventory must respond to: –list and –host [hostname]
The –list argument must return a JSON-encoded hash or dictionary containing all groups that are part of the inventory. The groups must include all host and child group information.
{
"httpd": {
"hosts": ["httpd1","httpd2"],
"vars": {
"httpd_port": 80
},
"children": ["cdn"]
},
"cdn": {
"hosts": ["cdn1","cdn2"],
"vars": {
"content_dir": "/var/www/content"
},
"children":[]
}
}
The –host [hostname] argument must return either an empty JSON hash or dictionary or a hash or dictionary of variables to make available to templates and playbooks.
{
"VAR001": "VALUE",
"VAR002": "VALUE",
}
Create inventory
To ccreate a simple Ansible inventory on the control node in /home/ansible/inventory containing node1 and node2
- keyboard_arrow_up
-
On the control host:
sudo su - ansible (if not already ansible user) touch /home/ansible/inventory echo "node1" >> /home/ansible/inventory echo "node2" >> /home/ansible/inventory
Modules in various languages
Unlike Puppet, Ansible does not require agent software to be installed and thus potentially leave residual bits on servers.
Modules are the “brains” of Ansible.
Various modules running on remote hosts provide the plumbing for other networking protocols, such as HTTP, runing on remote machines.
List of available modules, or locally:
ansible-doc -l
Press q to quit list, cursor up/down individual line, or space bar to page down.
Responses returned to the Ansible Control Server are in JSON messages.
Write Custome Module
Modules (hopefully written by following Module Development Guide) can be selected from various sources:
-
ansible-modules-core are writtin Python.
-
ansible-modules-extras developed by others have slightly lower use or priority.
Ansible Module development can be in any dynamic language, not just Python on the server.
- Simplejson library on *NIX.
Windows support
Ansible’s native Windows support uses Windows PowerShell remoting to manage Windows like Windows in the same Ansible agentless way that Ansible manages Linux like Linux.
-
Windows Remote PowerShell 2.0 enabled.
-
- Push and execute any PowerShell scripts you write
SSH into Hosts
To configure sudo access for Ansible on node1 and node2 such that Ansible may use sudo for any command with no password prompt.
- keyboard_arrow_up
-
Log in to node1 and edit the sudoers file to contain appropriate access for the ansible user:
ssh cloud_user@node1
sudo visudo
-
Add the following line to the file and save:
ansible ALL=(ALL) NOPASSWD: ALL
-
Repeate above steps for node2.
Next, verify that each managed node is able to be accessed by Ansible from the control node using the
pingmodule. Redirect the output of a successful command to/home/ansible/output. -
To verify each node, run the following as the ansible user from the control host:
ansible -i /home/ansible/inventory node1 -m ping
ansible -i /home/ansible/inventory node2 -m ping
-
To redirect output of a successful command to /home/ansible/output:
ansible -i /home/ansible/inventory node1 -m ping > /home/ansible/output
Python Ansible Control Server on Linux, not Windows
New major releases of Ansible come out approximately every two months, with release cycles of about four months.
PROTIP: Ansible was written in Python 2.6+ and open-sourced within GitHub’s ansible organization. Thus, it can run natively on NIX (Linux/Unix/Mac), but Windows not currently supported nor recommended. However, run virtual instances on a Windows, Mac, or other native OS if you want to use them to run Ansible.
To build Ansible from source on GitHub:
git clone https://github.com/ansible/ansible.git --recursive cd ./ansible make rpm sudo rpm -Uvh ./rpm-build/ansible-*.noarch.rpm
--recursive is needed because the repo contains sub-repos.
The “ansible_python_interpreter” variable in inventory points to the Python executable folder.
Python to WinRM
To enable Python to talk with Windows WinRM:
sudo pip install pywinrm
-
Test whether a connection can be made:
Test-WsMan 192.168.5.3
https://github.com/PowerShell/PowerShell/issues/1883
https://github.com/PowerShell/PowerShell/blob/master/docs/KNOWNISSUES.md#remoting-support (WinRM does not run within MacOS 10) PowerShell https://quizlet.com/178078947/ansible-devops-automation-mamun-flash-cards/
https://github.com/PowerShell/psl-omi-provider
VIDEO: Getting Started with Ansible on Windows 1h 23m Released 21 Jun 2016 by JP Toto (@jptoto, jptoto.jp) shows use of a Mac running Vagrant VirtualBox to emulate Windows.
Windows
This yaml file launches the hello.ps1 PowerShell script:
- name: Run Powershell Scripts
hosts: test
tasks:
- name: run a powershell script
script: scripts/hello.ps1
register: out
- debug: var=out
The script:
https://github.com/dstamen/Ansible/tree/master/ansible_powershell
See http://davidstamen.com/ansible/using-ansible-to-run-powershell-scripts/
To execute the script, run:
ansible-playbook powershell.yml -i hosts
Videos:
-
Using Ansible for your Windows Configuration Management by David O’Brien (by @david_OBrien, david-obrien.net) at NICconf 24 Feb 2016.
-
https://www.youtube.com/watch?v=jD2SHtfQHqs
Playbooks
Play behavior can be controlled several ways:
with_items, failed_when, changed_when, until, ignore_errors
Register Output to Variable
To capture the result or output of a task so that follow-on tasks can act accordingly:
tasks:
- shell: /usr/bin/whoami
register: username
- debug: msg="Host=, User="
- file: path=/home/myfile.txt
owner=Conditional Handlers
An example:
tasks:
- name: Deploy configuration file
template: src=templates/httpd.j2 dest=/etc/httpd/conf/httpd.conf
notify:
- Restart Apache
handlers:
- name: Restart Apache
service: name=httpd state=restartedNOTE: .j2 files are processed by Jinja2, the template engine for Python, which replace variables with data values in static files.
Another example:
---
- name: Testing forced handler
hosts: testsys_only
gather_facts: True
tasks:
- name: 'Run legacy script and power off'
debug: msg="Preparing for reboot"
changed_when: true
notify: Legacy sysprep
handlers:
- name: Enable Service1
service: name=service1 enabled=yes state=restarted
- name: Legacy sysprep
shell: /var/scripts/prep-reboot.shTo set a register to put result in a variable, then if the debug sees that a previous task failed, it would send a message.
tasks:
- command: ls /bad/path
register: result
ignore_errors: yes
- debug: msg="Failure!"
when: result|failedNOTE: Handlers don’t run until all playbook tasks have executed.
tasks:
- copy: src=files/httpd.conf
dest=/etc/httpd/conf/
notify:
- Apache Restart
handlers:
- name: Apache Restart
service: name=httpd state=restartedNOTE: A particular handler only executes once if needed.
NOTE: Handlers don’t run until all playbook tasks have executed.
Config. settings
Variables can be defined in different locations. Ansible looks for configuration variables in this sequence, and stops searching once it finds one.
- $ANSIBLE_CONFIG system environment variable
- ./ansible_cfg in current directory
- ~/ansible.cfg ($HOME directory of currently logged in account)
- /etc/ansible/ansible.cfg global config. file installed by default
ansible.cfg
Edit the file to make common changes, such as:
- inventory location from
/etc/ansible/inventory - SSH timeout from default 10 seconds
-fnumber of hosts acted upon (by forks) at the same time by Ansible. The default is 5. This can be overridden within a playbook by the serial keyword.
$ANSIBLE_CONFIG
An example $ANSIBLE_CONFIG environment variable from the full list is:
$ANSIBLE_FORKS=5
This sets the maximum number of parallel operations allowed on an Ansible server, determined through performance and capacity testing.
Include files
tasks:
- include: wordpress.yml
vars:
sitename: My Site
- include_vars: variables.ymlRoles
- https://bitbucket.org/fquffio/ansible-elasticsearch/src
- https://bitbucket.org/fquffio/ansible-kibana/src
- https://bitbucket.org/fquffio/ansible-iptables
Daemon Sets
Scalyr.com has a DaemonSet for Kubernetes monitoring.
Rolling updates
Ansible achieves zero-downtime deployments with multi-tear rolling updates to each specific node in a cluster.
This specifies taking 5 machines at a time out of a cluster:
- hosts: webservers
serial: 5
pre_tasks:
- name: take out of load balancer pool
local_action: command /usr/bin/take_out_of_pool
roles:
- common
- webserver
- monitored
post_tasks:
- name: add back to load balancer pool
local_action: command /usr/bin/add_back_to_pool
Social Community
- Twitter: @ansible by Red Hat, @robynbergeron
- https://groups.google.com/forum/#!forum/ansible-announce
- On a IRC client, select Destination: Freenode, and add channel #ansible.
- Ansible-Galaxy.com/explore/ is the community hub to find and share reusable Ansible content.
- Link to GitHub https://galaxy.ansible.com/accounts/github/login/
- Confirm email.
- AnsibleFest Atlanta September 24-26, 2019
Tutorials
Ansible Basics: Automation Technical Overview (DO007)
$10,000 10-day Ansible Automation Platform Boot Camp (DO710) for Linux administrators and developers to learn how to automate Linux system administration tasks with Ansible Automation Platform, manage complex automation workflows at scale, and evaluate automation performance. With enrollment is 1 year of Red Hat Learning Subscription Standard with unlimited access to all online courses and up to 5 certification exams.
DO007: ANSIBLE BASICS: AUTOMATION TECHNICAL OVERVIEW Create, scale, and manage automation with Red Hat Ansible Automation Platform with Ansible Basics: Automation Technical Overview (DO007).
EX374: RED HAT CERTIFIED SPECIALIST IN DEVELOPING AUTOMATION WITH ANSIBLE AUTOMATION PLATFORM EXAM This exam tests your ability to automate system administration tasks using Ansible Automation Platform.
RH294: Red Hat Linux Automation with Ansible (RH294) teaches how to automate provisioning, configuration, app deployment, and orchestration.
Certifications
Red Hat Certified Specialist in Managing Automation.
EX467: Red Hat Certified Specialist in Managing Automation with Ansible Automation Platform exam tests your ability to automate system administration tasks at scale using Ansible Automation Platform automation hub and automation controller.
EX417: Red Hat Certified Specialist in Microsoft Windows Automation with Ansible Exam A performance based exam to assess candidates’ skills and knowledge of managing Microsoft Windows® systems using Red Hat Ansible Automation Platform.
EX457: Red Hat Certified Specialist in Ansible Network Automation exam A performance-based test used to assess the skills and knowledge to manage network infrastructure using Red Hat® Ansible®.
EX447: Retired - Red Hat Certified Specialist in Advanced Automation: Ansible Best Practices exam A Red Hat Certified Specialist in Advanced Automation: Ansible Best Practices has validated mastery of Red Hat Ansible and knowledge of Ansible Tower.
Videos
Videos of AnsibleFest going back to 2016 in London and 2017 San Francisco.
MEH: Red Hat’s video channel and Red Hat Summit doesn’t have a playlist specifically for Ansible.
- ansible.com/quick-start-video provide your email because it is a high-level, high-flautin’ marketing pitch which introduces Ansible Tower proprietary software.
Tim Gerla of Ansibleworks:
-
Continuous Deployment with Ansible USENIX 38:38 on 11 Jul 2013
-
Hands-on Ansible Pluralsight 3h 53m video course 29 Dec 2015 by Aaron Paxson | @Neelixx | myteneo.net
-
Continuous Delivery Using Docker and Ansible Pluralsight video course 10 May 2016 by Justin Menga (@jmenga | pseudo.co.de) in 7h 13m creates Ansible files for a Python “TO DO” app using the Django REST framework. The files create Docker image.
-
Ansible and Docker by Patrick Galbraith from HP’s Advanced Technologies group.
Gwyn Price:
-
Ansible Playbook to create an RDS instance and get the endpoint 26 Nov 2015
-
Ansible Hands-On Training by Glen Jarvis
-
Getting Started With Jenkins edureka!
-
http://devopsguys.com in the UK
Misc
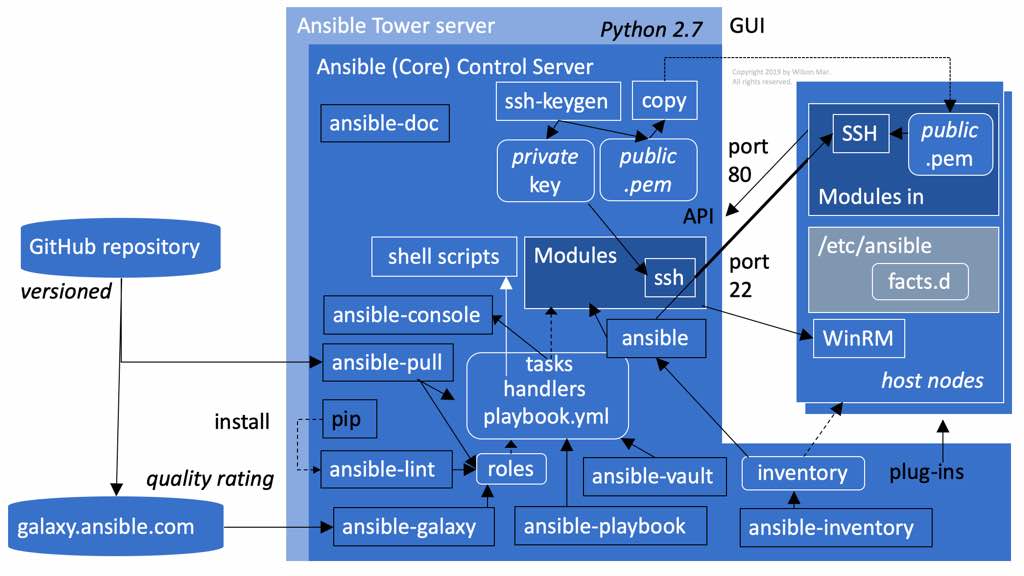
- From 2013 until October 11, 2017, Ansible Weekly newsletter at https://hvops.com/news/ansible
The diagram is based on https://www.ansible.com/how-ansible-works:
https://github.com/sthulb-attic/laptop-osx by @sthulb, an Amazon Solution Architect
https://hvops.com/articles/ansible-post-install/

- https://www.udemy.com/course/valaxy-devops/?referralCode=8147A5CF4C8C7D9E253F “100% Hands-on labs on how to create DevOps CI/CD pipelines using Git, Jenkins, Ansible, Docker and Kubernetes on AWS”</a> also on YOUTUBE
Resources
https://learning.oreilly.com/course/ansible-from-basics/9780137894949/
https://github.com/sandervanvugt/ansiblefundamentals
More on DevOps
This is one of a series on DevOps:
- DevOps_2.0
- ci-cd (Continuous Integration and Continuous Delivery)
- User Stories for DevOps
- Git and GitHub vs File Archival
- Git Commands and Statuses
- Git Commit, Tag, Push
- Git Utilities
- Data Security GitHub
- GitHub API
- Choices for DevOps Technologies
- Pulumi Infrastructure as Code (IaC)
- Java DevOps Workflow
- AWS DevOps (CodeCommit, CodePipeline, CodeDeploy)
- AWS server deployment options
- Cloud services comparisons (across vendors)
- Cloud regions (across vendors)
- Azure Cloud Onramp (Subscriptions, Portal GUI, CLI)
- Azure Certifications
- Azure Cloud Powershell
- Bash Windows using Microsoft’s WSL (Windows Subsystem for Linux)
- Azure Networking
- Azure Storage
- Azure Compute
- Digital Ocean
- Packer automation to build Vagrant images
- Terraform multi-cloud provisioning automation
-
Hashicorp Vault and Consul to generate and hold secrets
- Powershell Ecosystem
- Powershell on MacOS
- Jenkins Server Setup
- Jenkins Plug-ins
- Jenkins Freestyle jobs
- Docker (Glossary, Ecosystem, Certification)
- Make Makefile for Docker
- Docker Setup and run Bash shell script
- Bash coding
- Docker Setup
- Dockerize apps
- Ansible
- Kubernetes Operators
- Threat Modeling
- API Management Microsoft
- Scenarios for load
- Chaos Engineering

